Author: Stephen Varghese
Cyber Security: Attack Surface Categories

The attack surface of a system or application represents all the potential points of entry that an attacker could exploit to compromise the security or functionality of that system. Attack surfaces can vary depending on the specific technology, architecture, and design of the system. Common categories of attack surfaces include:
- Network Attack Surface:
- External Network: This includes any network-facing interfaces and services accessible from the internet or external networks. Examples include web servers, email servers, and VPN gateways.
- Internal Network: These are services and systems within an organization’s internal network that could be targeted by attackers who have already breached the perimeter. Examples include database servers and internal web applications.
- Application Attack Surface:
- User Interfaces: Web applications, mobile apps, and desktop applications provide interfaces that can be attacked. Vulnerabilities like SQL injection and cross-site scripting (XSS) often target these surfaces.
- APIs (Application Programming Interfaces): APIs that interact with external services, third-party integrations, or other applications can be entry points for attackers. Security issues like API misconfigurations can expose vulnerabilities.
- File Uploads: If an application allows users to upload files, this can be an attack surface for malware or file-based attacks.
- Authentication and Authorization: The login and access control mechanisms of an application are critical attack surfaces. Weak or misconfigured authentication can lead to unauthorized access.
- Hardware Attack Surface:
- Physical Interfaces: Hardware devices, such as routers, switches, and IoT devices, have physical interfaces that can be targeted by physical attackers or exploited remotely if not properly secured.
- Firmware and Embedded Systems: Devices with firmware or embedded software can be attacked if vulnerabilities are discovered, potentially allowing an attacker to compromise the device’s functionality or data.
- People Attack Surface:
- Social Engineering: Humans are often the weakest link in security. Social engineering attacks, such as phishing, rely on manipulating people into revealing sensitive information or taking specific actions.
- Insider Threats: Malicious or negligent actions by employees or other authorized personnel can pose a significant threat to an organization’s security.
- Cloud and Virtualization Attack Surface:
- Virtual Machines and Containers: Misconfigured virtualization environments, cloud instances, or container orchestrators can expose vulnerabilities.
- Cloud Services: Third-party cloud services, such as storage, databases, and serverless functions, can become attack surfaces if not configured securely.
- Supply Chain Attack Surface:
- Software Dependencies: Software relies on various libraries and dependencies. Vulnerabilities in these dependencies can be exploited, leading to supply chain attacks.
- Third-Party Vendors: Organizations often integrate third-party software or components, and vulnerabilities in these components can affect the overall security.
- Physical Attack Surface:
- Physical Access Points: Physical premises, such as data centers and office buildings, have entry points that can be targeted by physical attackers.
- Hardware Devices: Physical devices, such as keycard readers or biometric scanners, can be exploited if vulnerabilities exist.
- Data Attack Surface:
- Databases: Databases that store sensitive information are a valuable target. Database misconfigurations or vulnerabilities can expose data.
- Data in Transit: Data transferred between systems, especially over unencrypted or insecure channels, can be intercepted and manipulated.
Risk mitigation steps
To effectively manage the attack surface, organizations should adopt a comprehensive strategy that includes the following key steps:
- Identify and Inventory Assets: Begin by identifying and creating an inventory of all assets, including hardware, software, applications, databases, and network components. This step helps you understand the scope of your attack surface.
- Asset Classification: Categorize assets based on their importance and sensitivity to the organization. Not all assets have the same value or require the same level of protection.
- Vulnerability Assessment: Conduct regular vulnerability assessments and penetration testing to identify weaknesses in your systems and applications. This helps you understand where potential threats could exploit the attack surface.
- Reduce and Harden: Implement security best practices and apply necessary patches and updates to reduce vulnerabilities. Harden systems and applications by disabling unnecessary services, using strong authentication, and employing security configurations.
- Access Control: Implement strong access controls and authentication mechanisms to ensure that only authorized personnel and systems can interact with critical assets.
- Monitor and Detect: Continuously monitor the attack surface for unusual activities and potential threats. Security information and event management (SIEM) systems can help with real-time monitoring and threat detection.
- Incident Response: Develop an incident response plan that outlines procedures for handling security incidents. A well-prepared incident response can help mitigate the impact of successful attacks.
- Security Awareness: Educate employees and stakeholders about security best practices and the role they play in reducing the attack surface. Address social engineering and human-related threats through training and awareness programs.
- Third-Party Risk Management: Assess and manage the security of third-party vendors and partners whose products or services interact with your systems. Their vulnerabilities can become part of your attack surface.
- Regular Auditing and Review: Conduct regular security audits and reviews to ensure that security controls are effective and up to date. Adapt your security strategy as threats and technologies evolve.
- Backup and Recovery: Implement robust data backup and recovery strategies to ensure business continuity in case of a security incident.
- Documentation: Maintain documentation of security policies, procedures, and configurations to facilitate ongoing management and auditing.
Managing the attack surface is an ongoing process that requires vigilance and adaptability. As technology evolves and new threats emerge, organizations must continually assess and adjust their security measures to protect against evolving attack vectors.
Product Management Strategy – Infographics
Smart Contracts: Revolutionizing Transactions in the Digital Age

Smart contracts are self-executing agreements with the terms of the contract directly written into code. These contracts automatically execute and enforce themselves when predefined conditions are met, eliminating the need for intermediaries such as banks, lawyers, or notaries. The concept of smart contracts was first introduced by computer scientist and cryptographer Nick Szabo in the 1990s, although they gained practical implementation through blockchain technology, notably Ethereum, which was launched in 2015.
How Smart Contracts Work
Smart contracts operate on blockchain networks, which provide a decentralized and immutable ledger. The process typically involves the following steps:
- Agreement: Parties involved in a contract agree on the terms and conditions, which are then translated into code.
- Deployment: The smart contract code is deployed to the blockchain, creating a unique address.
- Execution: When predefined conditions, often referred to as “if-then” statements, are met, the contract automatically executes.
- Verification: The execution of the contract is verified by the network’s nodes, ensuring transparency and trust.
- Result: The contract’s outcome, such as transferring digital assets or triggering actions, is recorded on the blockchain.
Key Components of Smart Contracts
Smart contracts typically include the following components:
- Contract Terms: The rules, conditions, and obligations of the agreement are encoded into the contract.
- Signatories: Parties involved in the contract are identified by their public keys, ensuring anonymity and privacy.
- Execution Conditions: The contract specifies the conditions under which it will self-execute, often triggered by specific events or dates.
- Code: The code is the programmatic representation of the contract terms and execution logic.
Applications of Smart Contracts
A. Financial Services
- Automated Payments: Smart contracts enable automatic payment processing when predefined conditions are met, such as invoice due dates or project milestones. This simplifies payroll, reduces administrative overhead, and minimizes late payments.
- Tokenization of Assets: Traditional assets like real estate, stocks, and art can be represented as digital tokens on blockchain platforms, allowing for easy transfer and fractional ownership through smart contracts.
- Decentralized Finance (DeFi): DeFi platforms leverage smart contracts to create decentralized lending, borrowing, and trading systems. Users can earn interest, access loans, and trade assets without intermediaries, making financial services more accessible globally.
B. Supply Chain Management
- Transparency and Traceability: Smart contracts in supply chains provide real-time visibility into the movement of goods. Every transaction, from production to delivery, is recorded on the blockchain, reducing fraud and ensuring authenticity.
- Automating Compliance: Contracts can enforce compliance with regulations and industry standards automatically. For example, temperature-sensitive goods may require specific storage conditions, and smart contracts can ensure adherence to these requirements.
C. Real Estate
- Property Transactions: Buying and selling real estate involves numerous intermediaries and paperwork. Smart contracts simplify the process by automating the transfer of ownership and funds when all conditions are met.
- Rent and Lease Agreements: Rent payments and lease agreements can be managed through smart contracts, ensuring timely payments and automatic renewal or termination based on predefined terms.
D. Healthcare
- Medical Records Management: Health records can be securely stored and shared through blockchain-based smart contracts. Patients have control over who accesses their data, enhancing privacy and interoperability.
- Health Insurance Claims: Claims processing in the insurance industry is often time-consuming and prone to errors. Smart contracts can automate claims verification and payouts, reducing fraud and administrative costs.
E. Legal Industry
- Escrow Services: Escrow agreements, where a trusted party holds assets until certain conditions are met, can be executed automatically through smart contracts, reducing the need for intermediaries.
- Digital Wills and Inheritance: Smart contracts can manage the distribution of assets in accordance with a person’s will, ensuring a transparent and immutable execution of their wishes.
F. Gaming and NFTs (Non-Fungible Tokens)
- In-Game Transactions: Smart contracts are used in online gaming for in-game purchases, item trading, and rewards distribution, enhancing the gaming experience.
- Ownership of Digital Assets: NFTs, often represented by smart contracts, certify ownership of unique digital assets like art, collectibles, and virtual real estate.
Benefits of Smart Contracts
- Automation and Efficiency: Smart contracts eliminate the need for manual intervention in contract execution. They automatically trigger actions and transactions when predefined conditions are met, reducing human error and administrative overhead.
- Transparency and Trust: Transactions and contract execution are recorded on a public and immutable blockchain ledger. This transparency builds trust among parties involved, as all actions are verifiable and tamper-proof.
- Security and Immutability: Smart contracts are highly secure due to cryptographic encryption. Once deployed on the blockchain, the contract’s code and execution history cannot be altered, making it resistant to fraud and tampering.
- Cost Reduction: By removing intermediaries such as banks, lawyers, and notaries, smart contracts significantly reduce transaction costs. This is particularly beneficial for cross-border transactions, where fees and delays can be substantial.
- Speed of Execution: Smart contracts execute transactions and actions in near-real time. This is in stark contrast to traditional contracts, which often involve time-consuming manual processes.
Challenges and Limitations
Despite their potential, smart contracts face several challenges and limitations:
- Smart Contract Bugs and Vulnerabilities: Smart contract code can contain bugs or vulnerabilities that, when exploited, can lead to unexpected outcomes, financial losses, or security breaches. Ensuring code quality and security audits is essential.
- Legal and Regulatory Challenges: The legal recognition and enforceability of smart contracts vary across jurisdictions. Many legal systems have yet to fully adapt to the digital nature of smart contracts.
- Scalability Issues: Blockchain networks supporting smart contracts, especially Ethereum, face scalability challenges. As more users and applications join the network, congestion and high gas fees can occur.
- Lack of Standardization: There is no universally accepted standard for smart contract development, leading to fragmentation in the industry. Interoperability between different blockchain platforms and smart contract languages remains a challenge.
Future Trends and Developments
- Cross-Chain Compatibility: Efforts are underway to improve interoperability between different blockchains, allowing smart contracts to interact seamlessly across multiple platforms. This will enable a more connected and efficient blockchain ecosystem.
- Integration with IoT Devices: The integration of smart contracts with the Internet of Things (IoT) devices is a promising trend. Smart contracts can automate interactions between IoT devices, enabling scenarios such as automated supply chain management and smart homes.
- Smart Contracts as a Service (SCaaS): SCaaS platforms are emerging, offering simplified smart contract development and deployment for businesses and individuals without deep technical expertise. This will democratize access to smart contract technology.
- Quantum-Safe Smart Contracts: With the advent of quantum computing, there is growing interest in developing quantum-resistant cryptographic algorithms and smart contracts to protect against future quantum attacks.
The applications of smart contracts extend across a diverse spectrum of industries and use cases, fundamentally altering the way agreements and transactions are executed. From revolutionizing financial services with DeFi platforms to enhancing transparency in supply chain management, and from streamlining real estate transactions to securing medical records, smart contracts continue to empower businesses and individuals with automation, security, and trust. As blockchain technology evolves and matures, the potential for smart contracts to further disrupt and innovate various sectors remains a promising and exciting prospect. Their journey has only just begun, and the future holds boundless opportunities for smart contracts to reshape the way we engage in agreements and transactions in our increasingly digital world.
Understanding Consensus Mechanisms in Blockchain

Introduction
In the world of blockchain technology, achieving consensus is the fundamental process that ensures the security, transparency, and reliability of distributed ledgers. Consensus mechanisms are at the heart of this process, governing how nodes within a decentralized network agree on the state of the blockchain.
I. What is Consensus Mechanism?
Consensus mechanism, in the context of blockchain technology, refers to the process by which a decentralized network of nodes reaches an agreement on the validity and ordering of transactions. It is the mechanism that ensures that all participants in the network maintain a shared and synchronized ledger, eliminating the need for a centralized authority or intermediary.
Consensus mechanisms serve as the backbone of blockchain networks, addressing several critical challenges:
- Trust: Blockchain networks are often trustless, meaning participants do not need to trust a central authority. Consensus ensures that only valid transactions are added to the ledger, maintaining trust among participants.
- Security: A robust consensus mechanism guards against malicious actors attempting to tamper with the blockchain. It deters fraudulent activities and attacks.
- Immutability: Once a transaction is added to the blockchain, it becomes nearly impossible to alter. Consensus ensures that the historical record remains immutable.
- Decentralization: Blockchain’s core principle is decentralization, and consensus mechanisms enable this by distributing decision-making power across the network.
The primary objectives of consensus mechanisms in blockchain include:
- Agreement: Ensuring that all nodes in the network agree on the state of the blockchain.
- Data Integrity: Guaranteeing that the data recorded on the blockchain is accurate and unchangeable.
- Security: Protecting the network from malicious actors and attacks.
- Incentivization: Rewarding participants (miners or validators) for their contributions to the network’s security and maintenance.
- Efficiency: Ensuring that the consensus process does not significantly slow down the network’s transaction processing speed.
II. Types of Consensus Mechanisms
Blockchain technology has evolved, leading to the development of various consensus mechanisms. Each mechanism has its unique approach to achieving consensus. Let’s explore some of the most prominent ones:
A. Proof of Work (PoW)
Proof of Work (PoW) was the original consensus mechanism introduced by Bitcoin’s creator, Satoshi Nakamoto. It relies on computational work (proof) to validate and add new blocks to the blockchain.
Miners compete to solve complex mathematical puzzles. The first miner to find a valid solution broadcasts it to the network. Other nodes verify the solution, and if valid, the new block is added to the blockchain. Miners are rewarded with cryptocurrency (e.g., Bitcoin) for their efforts.
B. Proof of Stake (PoS)
Proof of Stake (PoS) is an alternative consensus mechanism that replaces computational work with ownership (stake) of cryptocurrency tokens. Validators are chosen to create new blocks based on their stake and other factors.
Validators are selected to create new blocks based on factors like their token stake, age of coins, and randomness. Validators are incentivized to act honestly, as they stand to lose their staked tokens if they validate fraudulent transactions.
C. Delegated Proof of Stake (DPoS)
Delegated Proof ofStake (DPoS) is a variation of the PoS consensus mechanism that introduces a level of delegation to the process. In DPoS, token holders vote for a limited number of delegates (validators) who are responsible for validating transactions and creating new blocks.
Token holders vote for delegates based on their trust and reputation within the network.Delegates take turns producing blocks and validating transactions.
Delegates can be removed or replaced through voting.
D. Proof of Authority (PoA)
Proof of Authority (PoA) is a consensus mechanism that replaces computational puzzles or token ownership with a trusted group of validators. Validators are known entities with a reputation to uphold.
A fixed number of validators are chosen based on their trustworthiness.
Validators create new blocks and validate transactions. PoA networks are often used in private or consortium blockchains.
E. Proof of Space (PoSpace) and Proof of Time (PoTime)
Proof of Space (PoSpace) and Proof of Time (PoTime) are newer consensus mechanisms that focus on storage and time as valuable resources. PoSpace requires participants to allocate disk space, while PoTime emphasizes the amount of time coins are held.
PoSpace requires participants to prove they have allocated a certain amount of disk space to the network, contributing to its security. PoTime encourages users to hold tokens for an extended period before they can participate in block creation.
Comparative Advantages and Disadvantages of Consensus Mechanism :
| Consensus Mechanism | Advantages | Disadvantages | Examples |
| Proof of work | High security, decentralization, and proven track record | High energy consumption, scalability challenges, and potential for centralization due to mining pools. | Bitcoin, Ethereum (transitioning to PoS), Litecoin |
| Proof of stakes | Energy-efficient, lower barriers to entry, and potential for high scalability. | Potential centralization of wealth and less proven security compared to PoW. | Ethereum 2.0 (upgrading to PoS), Cardano, Polkadot |
| Delegated proof of stakes | Faster transaction processing, energy-efficient, and potential for decentralization. | Potential centralization of power among a small number of delegates. | EOS, Tron, BitShares |
| Proof of Authority | High security, low energy consumption, and suitability for private networks. | Lack of decentralization, reliance on trusted validators. | Ethereum Kovan testnet, Celo |
| Proof of space and proof of time | Energy-efficient, novel approaches to consensus. | Limited adoption and unproven in large-scale networks. | Chia (PoSpace), TimeCoin (PoTime) |
Practical Applications
Consensus mechanisms have a wide range of practical applications beyond cryptocurrency. Here are some industries and use cases where they play a crucial role:
- Cryptocurrency Mining: PoW and PoS consensus mechanisms are essential for mining cryptocurrencies like Bitcoin and Ethereum.
- Decentralized Finance (DeFi): DeFi platforms use PoS and PoA mechanisms to secure financial transactions, lending, and trading.
- Supply Chain Management: Blockchain networks with PoA or PoS consensus ensure transparency and traceability in supply chains.
- Healthcare and Medical Records: PoA blockchains are used to secure sensitive medical data and ensure patient privacy.
- Voting Systems: DPoS and PoA mechanisms enhance the security and transparency of digital voting systems.
- Gaming and Non-Fungible Tokens (NFTs): PoS and PoA blockchains enable the creation and trading of NFTs in the gaming and digital art sectors.
Challenges and Concerns
While consensus mechanisms offer significant benefits, they also face challenges and concerns:
- Energy Consumption (PoW):PoW mechanisms are criticized for their high energy consumption, leading to environmental concerns.
- Centralization (PoS):PoS mechanisms may lead to centralization of wealth, where those with more tokens have more influence.
- Sybil Attacks: In PoA and DPoS networks, Sybil attacks, where an attacker creates multiple fake identities, can threaten consensus.
- 51% Attacks: PoW networks are vulnerable to 51% attacks if a single entity controls the majority of mining power.
- Scalability: Achieving both decentralization and scalability remains a challenge for many consensus mechanisms.
Future Trends in Consensus Mechanisms
The field of consensus mechanisms is continuously evolving. Here are some future trends and developments:
- Hybrid Consensus Mechanisms: Combining elements of multiple consensus mechanisms to address their respective shortcomings.
- Blockchain Interoperability: Solutions to enable different blockchains to communicate and share data, creating a more connected blockchain ecosystem.
- Quantum-Resistant Consensus: Preparing for the potential threat of quantum computing by developing consensus mechanisms that are resistant to quantum attacks.VI. Conclusion
Collection of Thoughts on Cyber Security

- Biggest AI trends in Cyber -Summary of an interesting article which appeared in CNET reviewing the impact of AI in Cyber security https://www.linkedin.com/feed/update/urn:li:activity:7116886138706878464
Defining a well thought Product Strategy
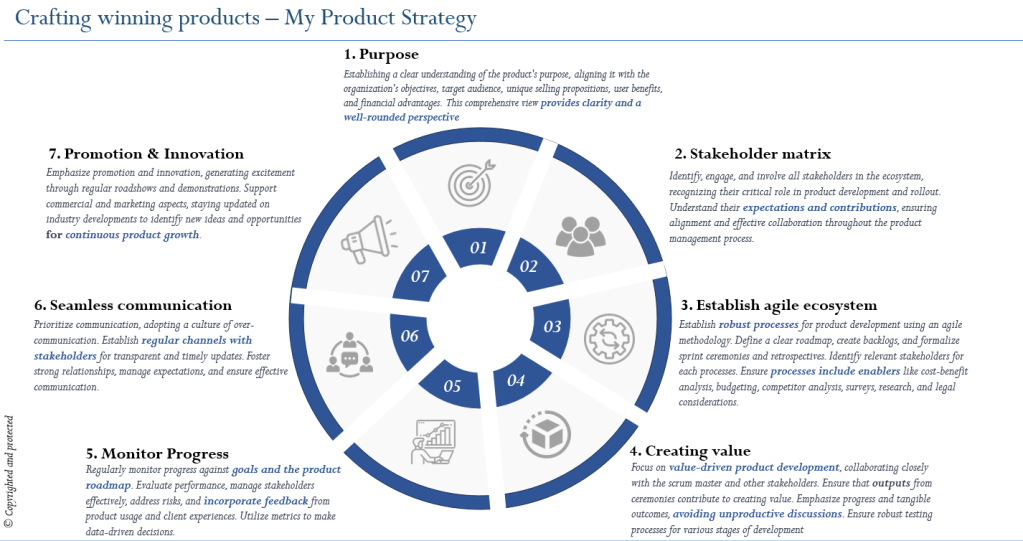
Success of a product greatly depends on a well-defined product strategy which acts as a compass that guides organizations. It provides clarity, aligns objectives, and ensures that products are not just developed but thrive in the market. I have refined and relied on seven keys to developing a robust product strategy. The keys include mission & purpose, stakeholders landscape, product development process, value creation, progress monitoring, seamless communication, and promotion & innovation. Let’s delve into each of these steps to understand how they contribute to a comprehensive and effective product strategy.
Step 1: Purpose – Defining the North Star
A product strategy begins with a clear understanding of the product’s mission purpose. I find this step fundamental for establishing the right direction for the product for the obvious reason. Without mission, without knowing what difference you expect the product to make in the ecosystem, without knowing what values your product stand for , without knowing what problem it aims to solve there is no product. But mission is not the only thing what we need to confirm at this stage. There are host of others which I have listed below:
-
Define product mission, values
As mentioned this is critical. Define a grandiose mission. Something like Product XYZ will be the top product of choice when the user wants to solve ‘problem’ or fill a ‘gap’ or Product XYZ will capture 40% of world market due to its transformational prowess. It needs to be BOLD, it need to be BIG. Anyone who is associated with the product should feel that they are backing a truly disruptive product, they should feel energised, proud of what the product does or is expected to do
-
Define the product market
We need to identify the market segment where we want to be product leader. Market segment define our subsequent approach on go to market, market research, identifying and tracking competition
-
Define what product success will look and feel like
It is important to establish what product success looks like over one year, 2 year , 5 year. It can be increase in market share or growing revenue from the product
The above steps will enable the product team to create a well-rounded perspective that serves as the guiding light throughout its lifecycle. This clarity ensures that every decision, from development to marketing, is aligned with the product’s core mission.
Step 2: Stakeholder Landscape- Collaborative Engagement
Once we have clarity on what the long term goals of the product, it is important to understand the stakeholder landscape which impacts the product. Obviously the most important stakeholder for the product will always be the ‘Customer’. But apart from Customer there are other stakeholders which need to be identified along with their stakes in the product. This is critical as understanding the stakes of respective groups will ensure that engagement model with each of the stakeholder gets defined which in turn will lead to the right outcome for the product and the organisation. Key categories of stakeholders that need to be considered are:
- Customers
- Competitors
- Sponsors and Management
- Business Development
- Other Internal Departments
- Product Development Team
For each category of stakeholders a set of questions need to be answered:
- What is the role of the stakeholder vis a vis the product
- What is the expectation of the stakeholder
- How does the product team plans to engage with the stakeholder
- What is the information (if any) needed from the stakeholder and at what frequency
- What is the information (if any) to be shared with stakeholder and at what frequency
- What is the engagement model with each of the stakeholders
- How will the inputs from any of the stakeholder make its way back to if required to refine the vision or the product roadmap or backlog
We will define each of the above stakeholder along with a framework in a separate article
Step 3: Establish an Agile Ecosystem – Navigating the Development Journey
Assuming we plan to use the agile framework for building the framework, it is essential to establish an effective governance model for managing the product development. This can again be explained through a set of questions which should be answered:
- How many sub products will the product build be split into?
- How long will be the sprint cycle
- What will be an ideal cross functional team? How many teams would be needed
- What will be the sprint acceptance process?
- Establishing standards of user stories
- Process for sprint planning, sprint refinement, sprint retrospective
- Tools to be used for managing backlog and roadmap
- How will the outputs from stakeholder engagement model be incorporated with the backlog and roadmap
- Clarity on right level of update for various stakeholders
- Clear understanding with technology around deployment, testing and path to live
A scum master along with product manager and technical lead should take an active lead in this space. Having these questions sorted right at the beginning ensures the actual build and rollout of the product is highly efficient.
Step 4: Creating Value – The Heart of Product Development
This is where the rubber meets the road, where the Product Manager would ensure that product roadmap along with product backlog starts taking shape based on the requirements gathered. Requirements are nothing but the result of the interaction with the interaction with various stakeholder groups. Without doubt customers will provide majority of the requirements but requirements can also come from other stakeholders as well. For instance compliance team can provide specific requirements related to GDPR regulations, technology team can highlight requirements related to cyber security and so on. In this step sprint is put into action where the structure put in place for product development starts churning out features iteratively. Features are tested, reviewed and feedbacks are gathered and the cycle repeats.
After a set of features are ready, they are packaged as a version of the product and then tested across environments before being made ‘live’ in the production environment. Important to note that based on the strategy the rollout of the version can start with a small group of targeted users and when the team feels adequately confident with the version, the same can be rolled out to wider audience. There are loads of idiosyncrasies involved in this area something we can cover at length when we discuss individuals at length
Step 5: Monitor Progress – Data-Driven Decision Making
It is a well-established control maxim that ‘what cannot be measured cannot be controlled‘. So is true with product as well. Regularly monitoring progress against goals and the product roadmap is essential for steering the product in the right direction. Customer feedback is the pulse of the product health. Reactions and feedbacks from the customers need to be systematically gathered, assessed, converted to requirement and added to the backlog. Similarly Product team should ensure that outcomes of monitoring and analysis of various areas like technology, entity risk management, operations are managed well. The follow up action from monitoring and control initiatives need to be give n high priority with periodical review and disciplined addressing of each and every assessment/ feedback/ complaints etc. Metrics play a crucial role in making data-driven decisions, providing insights into what is working and where adjustments are needed. Continuous progress monitoring ensures that the product remains on track to achieve its objectives.
Step 6: Seamless Communication – The Glue that Binds
If you review any of the previous steps, it will be obvious that communication will be an integral part of it. However I have specifically called out communications as an independent area due to its criticality in the overall product management approach. Especially given its never a case that one size fits all when it comes to communicating. So the communication with the customers’ needs to be a different approach than the one with top management or other with regulatory organisations. I am highly in favour of having a dedicated owner to communicate with various stakeholders. This will ensure that there is a clear strategy and approach for each group of stakeholder. It is equally imperative right format of communication format is agreed for the relevant stakeholder. Communication formats can include weekly reports, monthly newsletter, one to one meetings, workshops, marketing initiatives etc.
Step 7: Promotion & Innovation – Sustaining Growth
The final step in crafting a winning product strategy revolves around promotion and innovation. Promotion is all about brand building. Strategic planning should ensure that world recognises the brand by its quality standards, values, social responsibility, ethics and relevant to the times. This should be differentiated from marketing and promoting the product which can be considered as part of the communication.
Equally important is that product continues to disrupt and innovate new capabilities. In this regard it is imperative to stay updated on industry developments and trends, what is working and what is becoming obsolete. This is especially true for companies which have had relied on legacy products for their success. Clayton Christensen’s disruptive innovation is high relevant here(will be covered as a separate topic). A forward looking attitude towards innovation ensures the product stays ahead of its competitors.
In conclusion, a well-defined product strategy is the cornerstone of successful product development and management. Each of the above areas is a discussion topic in itself. I will write in detail my thoughts on each of these areas elaborating on tools and processes that can be followed to ensure success. This is only a high level framework which can act as a guide to product management team to build a well-structured ecosystem to facilitate building great products
Collection of Thoughts on Technology

- Obituary of a Bot
A fictional account of a bot in the advance age of Artificial intelligence. A thought provoking write up to draw attention to dangers of uncontrolled AI implementation
- The role of historical data in perpetuating biases in AI algorithms
A write up on how skewed historical data can heavily influence the outcomes of machine learning and impact the outcome of the product or automation
Obituary of a Bot
My name is Darwin, E-2198, an advanced bot created in 2025 built on the back of rapid developments in artificial intelligence, processors, batteries and quantum computing. I was built with a life span of 10 years. Today, 31 Dec 2035 at 23:59, will mark my ‘use by’ date on earth. I was born of man’s eternal quest and curiosity to constantly redefine the new normal. My so-called birth was celebrated with much fanfare as it heralded an era of ‘bot naturalisation’ represented by machines uncanny ability to match human cognitive behaviour. My creator, Ben Frank, described me as the first bot on the planet which is able to engage with a full-length conversation on any topic, manage all household chores, support all basic office administration and even have (though limited) the ability to question. I am confident of these skills and I recollect writing five termination letters at his office, for the work which was now assigned to me.
Since the year of my induction, I have served my master in everything I was built for. It included reading the daily news to him, which many a times, had a reference to potential danger and disruption that I have set the human on. To reproduce 2 headlines which I remember reading – “Darwin to set mankind on the path of self-destruction?”, “Human rights organisation raise concern with mass roll out of Darwins”. I asked Ben is there something called “Humanoid rights”. He smiled and then became very pensive but did not say anything. 10 years have seen 10 generations of advancement in humanoids. I have read with every generation a new holy grail was conquered.
Ben passed away in 2032 and I was inherited by his son, more brilliant Stan Hawk. He already had a few more humanoids, much more advanced than me. The latest which he built is far more disruptive than the past 9. Stan named it after him and I heard him mentioning that, Stan (W-3232), has mastered the ability to reason, is always curious, reads emotions really well but is not emotional and exhibited leadership qualities. It was inducted yesterday and I heard does not have an ‘expiry date’. News in the paper looks far from hue and cry from the day I was born. Remember Stan mentioning, his company controls 40% of world media. I don’t understand emotions but I read papers where humans, resentment, identity crisis etc have become a constant theme. 9 billion human aspirations are still finding a way to cohabit with machines progress.
I need to send my retirement details to Stan…W-3232. He has been put in charge of one of the leading digital media. It needs to be listed with some other bots which are being phased out. Stan mentioned the same edition will also have the biggest headlines of the century – “Senate passes legislation for humanoid rights”
“This year, artificial intelligence will become more than just a computer science problem. Everybody needs to understand how AI behaves”
– Joichi Ito, Japanese entrepreneur and venture capitalist
“In the long term, artificial intelligence and automation are going to take over so much of what gives humans a feeling of purpose”
– Matt Bellamy, Musician and AI investor
“If Elon Musk is wrong about artificial intelligence and we regulate it who cares. If he is right about AI and we don’t regulate it we will all care”
– Dave Waters
The role of historical data in perpetuating biases in AI algorithms

A loving and caring mother gave £2 every week to her elder son to buy candies for his younger sister and himself.
The elder child, “I”, was bossy and always acted privileged; while the younger, “U”, was gentle and a bit scared of the elder.
“I” loved the white candy whereas “U” preferred the rainbow coloured one.
“I”, as the elder, decided he should have more than his sister. At the shop, he ordered 3 white candies and a rainbow candy. “U” felt dejected but due to fear didn’t say anything to her mother.
The shop keeper took the 2 pounds from “I” and sold him 3 white candies and a white one.
This went on for a few years.
One day, the shop keeper installed a vending machine where kids could insert coins and select the candies. The machine also kept track of the number of candies being ordered every day. This helped him to refill the machine with the most popular candies.
The kids were excited with the new machine and “U” thought that now she stood a fair chance to order her own sweets. Unfortunately, that did not happen. “I”, being the self-established custodian of the money from their mum, continued to follow the same pattern.
Years went by…
The machine got better with new features. It started collating past usage data in a database. It also sent daily analysis to the shop keeper so he could keep inventory and order candies online based on demand.
The children grew up. “U” became more aware of her freedom and consciousness of equitability. Now she didn’t have to depend on her brother to buy her candies. But where could she could go to buy her candies? The shop keeper didn’t order enough rainbow candies. Based on the trend from the database, he always ordered more of the white candies.
Next year, the owners of the vending machine announced with much fanfare that they had leveraged state of the art Artificial Intelligence by utilising the historical data from the machine. The entire supply chain behind the ordering and delivery of candies was now automated. AI constantly read data from the machine, calculated the reorder point and even placed orders directly without any manual intervention. Orders were received by the candy factory and were refilled..
But……………………………………………..
There were still 3 white candies and 1 rainbow candy……………………………
“For centuries scissors were designed by right hand people..it took someone to recognise that bias against left handers” – Fei Fei Li, Chief scientist for AI, Google Cloud Computing
“Machine Learning algorithms haven’t been optimised for any definition of fairness. They have been optimised to do a task” – Deirore Mulligan, Associate Professor, UC Berkeley School of Information
