Category: Technology
Collection of Thoughts on Technology

- Obituary of a Bot
A fictional account of a bot in the advance age of Artificial intelligence. A thought provoking write up to draw attention to dangers of uncontrolled AI implementation
- The role of historical data in perpetuating biases in AI algorithms
A write up on how skewed historical data can heavily influence the outcomes of machine learning and impact the outcome of the product or automation
Obituary of a Bot
My name is Darwin, E-2198, an advanced bot created in 2025 built on the back of rapid developments in artificial intelligence, processors, batteries and quantum computing. I was built with a life span of 10 years. Today, 31 Dec 2035 at 23:59, will mark my ‘use by’ date on earth. I was born of man’s eternal quest and curiosity to constantly redefine the new normal. My so-called birth was celebrated with much fanfare as it heralded an era of ‘bot naturalisation’ represented by machines uncanny ability to match human cognitive behaviour. My creator, Ben Frank, described me as the first bot on the planet which is able to engage with a full-length conversation on any topic, manage all household chores, support all basic office administration and even have (though limited) the ability to question. I am confident of these skills and I recollect writing five termination letters at his office, for the work which was now assigned to me.
Since the year of my induction, I have served my master in everything I was built for. It included reading the daily news to him, which many a times, had a reference to potential danger and disruption that I have set the human on. To reproduce 2 headlines which I remember reading – “Darwin to set mankind on the path of self-destruction?”, “Human rights organisation raise concern with mass roll out of Darwins”. I asked Ben is there something called “Humanoid rights”. He smiled and then became very pensive but did not say anything. 10 years have seen 10 generations of advancement in humanoids. I have read with every generation a new holy grail was conquered.
Ben passed away in 2032 and I was inherited by his son, more brilliant Stan Hawk. He already had a few more humanoids, much more advanced than me. The latest which he built is far more disruptive than the past 9. Stan named it after him and I heard him mentioning that, Stan (W-3232), has mastered the ability to reason, is always curious, reads emotions really well but is not emotional and exhibited leadership qualities. It was inducted yesterday and I heard does not have an ‘expiry date’. News in the paper looks far from hue and cry from the day I was born. Remember Stan mentioning, his company controls 40% of world media. I don’t understand emotions but I read papers where humans, resentment, identity crisis etc have become a constant theme. 9 billion human aspirations are still finding a way to cohabit with machines progress.
I need to send my retirement details to Stan…W-3232. He has been put in charge of one of the leading digital media. It needs to be listed with some other bots which are being phased out. Stan mentioned the same edition will also have the biggest headlines of the century – “Senate passes legislation for humanoid rights”
“This year, artificial intelligence will become more than just a computer science problem. Everybody needs to understand how AI behaves”
– Joichi Ito, Japanese entrepreneur and venture capitalist
“In the long term, artificial intelligence and automation are going to take over so much of what gives humans a feeling of purpose”
– Matt Bellamy, Musician and AI investor
“If Elon Musk is wrong about artificial intelligence and we regulate it who cares. If he is right about AI and we don’t regulate it we will all care”
– Dave Waters
The role of historical data in perpetuating biases in AI algorithms

A loving and caring mother gave £2 every week to her elder son to buy candies for his younger sister and himself.
The elder child, “I”, was bossy and always acted privileged; while the younger, “U”, was gentle and a bit scared of the elder.
“I” loved the white candy whereas “U” preferred the rainbow coloured one.
“I”, as the elder, decided he should have more than his sister. At the shop, he ordered 3 white candies and a rainbow candy. “U” felt dejected but due to fear didn’t say anything to her mother.
The shop keeper took the 2 pounds from “I” and sold him 3 white candies and a white one.
This went on for a few years.
One day, the shop keeper installed a vending machine where kids could insert coins and select the candies. The machine also kept track of the number of candies being ordered every day. This helped him to refill the machine with the most popular candies.
The kids were excited with the new machine and “U” thought that now she stood a fair chance to order her own sweets. Unfortunately, that did not happen. “I”, being the self-established custodian of the money from their mum, continued to follow the same pattern.
Years went by…
The machine got better with new features. It started collating past usage data in a database. It also sent daily analysis to the shop keeper so he could keep inventory and order candies online based on demand.
The children grew up. “U” became more aware of her freedom and consciousness of equitability. Now she didn’t have to depend on her brother to buy her candies. But where could she could go to buy her candies? The shop keeper didn’t order enough rainbow candies. Based on the trend from the database, he always ordered more of the white candies.
Next year, the owners of the vending machine announced with much fanfare that they had leveraged state of the art Artificial Intelligence by utilising the historical data from the machine. The entire supply chain behind the ordering and delivery of candies was now automated. AI constantly read data from the machine, calculated the reorder point and even placed orders directly without any manual intervention. Orders were received by the candy factory and were refilled..
But……………………………………………..
There were still 3 white candies and 1 rainbow candy……………………………
“For centuries scissors were designed by right hand people..it took someone to recognise that bias against left handers” – Fei Fei Li, Chief scientist for AI, Google Cloud Computing
“Machine Learning algorithms haven’t been optimised for any definition of fairness. They have been optimised to do a task” – Deirore Mulligan, Associate Professor, UC Berkeley School of Information
Blockchain and Distributed Ledger Technologies – An Overview

Wikipedia describes blockchain as “a decentralized, distributed, and often public, digital ledger consisting of records called blocks that are used to record transactions across many computers so that any involved block cannot be altered retroactively, without the alteration of all subsequent blocks.”
Blockchain is a distributed ledger technology (DLT) that was initially introduced as the underlying technology behind Bitcoin, the first cryptocurrency. It is a digital system for recording the transaction of assets in which the transactions and their details are recorded and stored across multiple locations or nodes on a network. Unlike traditional centralized databases, where a single entity (like a bank or a company) controls and maintains the database, DLT distributes the ledger among multiple participants in a decentralized and often trustless manner.
Blockchain technology was introduced in a whitepaper by an anonymous person or group of people using the pseudonym Satoshi Nakamoto in 2008. The whitepaper, titled “Bitcoin: A Peer-to-Peer Electronic Cash System,” outlined the concept of a decentralized digital currency, Bitcoin, and the blockchain as its underlying technology. The Bitcoin network went live in 2009 with the release of the Bitcoin software. It allowed users to make peer-to-peer transactions without the need for intermediaries like banks.
Ethereum, a blockchain platform, was launched by Vitalik Buterin and others. Ethereum introduced smart contracts, which are self-executing contracts with the terms directly written into code. This expanded the use cases of blockchain beyond cryptocurrencies.
Key characteristics of DLT include:
- Decentralization: DLT operates on a network of nodes (computers) that are distributed across various locations. These nodes work together to validate and record transactions. This decentralization reduces the risk of a single point of failure and enhances security.
- Transparency: Most DLTs are designed to be transparent, meaning that all participants on the network can view the ledger’s contents. This transparency helps in trust-building among network participants
- Immutability: Once data is recorded on a DLT, it is extremely difficult to alter or delete. This immutability is achieved through cryptographic techniques and consensus mechanisms.
- Security: DLTs use cryptographic algorithms to secure data and transactions. The decentralized nature of the network also makes it more resilient to attacks.
- Consensus Mechanisms: DLTs employ consensus mechanisms to validate and agree on the state of the ledger. Common consensus mechanisms include Proof of Work (PoW), Proof of Stake (PoS), and Byzantine Fault Tolerance (BFT)
Difference Between Blockchain and DLT:
Blockchain and Distributed Ledger Technology (DLT) are related concepts, but they are not interchangeable. Here are the key differences:
| Blockchain | DLT | |
| Scope | A specific type of DLT that uses a chain of blocks to record transactions or data. It is a subset of DLT. | A broader category that encompasses various distributed ledger technologies, including blockchain. DLT refers to any system where data is stored and maintained across multiple nodes or locations. |
| Centralization | Typically decentralized, with no central authority controlling the network. | Can be either centralized, decentralized, or semi-decentralized, depending on the specific implementation and use case. |
| Consensus Mechanisms | Often uses consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to validate and add transactions to the chain | Can use various consensus mechanisms, including but not limited to PoW and PoS, depending on the design and requirements. |
| Use Cases | Primarily associated with cryptocurrencies, smart contracts, and DApps. | Used in a wide range of applications, including supply chain management, identity verification, healthcare, and more. |
Application Programming Interface (API)
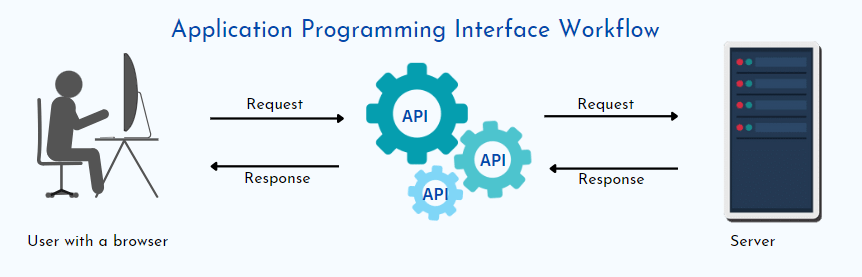
An API, or Application Programming Interface, is a set of rules and protocols that allows different software applications or systems to communicate and interact with each other. It defines the methods and data formats that applications can use to request and exchange information, enabling them to work together seamlessly. APIs are fundamental to modern software development and are used in various contexts, including web development, mobile app development, and integration between different software systems. Here’s an overview of APIs:
Key Characteristics of APIs:
- Abstraction: APIs provide an abstraction layer that hides the underlying complexity of software systems. Developers can interact with an API without needing to understand the internal workings of the system it connects to.
- Standardization: APIs are standardized to ensure consistency and compatibility between different software components. They define a clear set of rules and conventions for communication.
- Interoperability: APIs enable different software applications, regardless of their platforms or programming languages, to communicate and work together. This promotes interoperability and integration.
- Modularity: APIs promote modularity in software design. Developers can build complex systems by combining smaller, reusable components with well-defined APIs.
Types of APIs:
- Web APIs: These are APIs that use HTTP or HTTPS protocols to enable communication over the internet. Web APIs are commonly used for web services, allowing applications to access data or services hosted on remote servers. REST (Representational State Transfer) and SOAP (Simple Object Access Protocol) are common web API architectural styles.
- Library APIs: Library APIs provide a set of functions, procedures, or classes that developers can use within their own code. These APIs are often packaged in software libraries or frameworks, making it easier for developers to leverage existing functionality.
- Operating System APIs: Operating systems provide APIs that allow applications to interact with system resources and services. Examples include Windows API for Windows operating systems and POSIX API for Unix-like systems.
- Hardware APIs: These APIs provide access to hardware components such as graphics cards, printers, and sensors. Developers can use hardware APIs to control and utilize these devices in their software applications.
Common Use Cases for APIs:
- Data Integration: APIs are frequently used to connect different data sources and systems, allowing applications to retrieve, update, and synchronize data in real-time.
- Third-Party Services: Many applications leverage third-party APIs to access external services, such as payment processing, social media integration, mapping and geolocation, and more.
- Microservices: In microservices architectures, APIs play a crucial role in enabling communication between microservices, allowing them to function as independent and scalable units.
- Mobile App Development: Mobile apps often use APIs to access backend services, retrieve data, and provide features like location-based services, push notifications, and social media sharing.
- Web Development: APIs are used to create interactive and dynamic web applications by enabling client-side JavaScript code to communicate with server-side services and databases.
- IoT (Internet of Things): APIs enable IoT devices to communicate with each other and with cloud-based platforms for data collection, analysis, and control.
APIs are a fundamental building block of modern software development, enabling developers to create feature-rich, interconnected applications that can access a wide range of services and data sources. Effective API design and documentation are essential to ensure that developers can use APIs easily and securely.
