Tag: Cyber Security
Cyber Security: Attack Surface Categories

The attack surface of a system or application represents all the potential points of entry that an attacker could exploit to compromise the security or functionality of that system. Attack surfaces can vary depending on the specific technology, architecture, and design of the system. Common categories of attack surfaces include:
- Network Attack Surface:
- External Network: This includes any network-facing interfaces and services accessible from the internet or external networks. Examples include web servers, email servers, and VPN gateways.
- Internal Network: These are services and systems within an organization’s internal network that could be targeted by attackers who have already breached the perimeter. Examples include database servers and internal web applications.
- Application Attack Surface:
- User Interfaces: Web applications, mobile apps, and desktop applications provide interfaces that can be attacked. Vulnerabilities like SQL injection and cross-site scripting (XSS) often target these surfaces.
- APIs (Application Programming Interfaces): APIs that interact with external services, third-party integrations, or other applications can be entry points for attackers. Security issues like API misconfigurations can expose vulnerabilities.
- File Uploads: If an application allows users to upload files, this can be an attack surface for malware or file-based attacks.
- Authentication and Authorization: The login and access control mechanisms of an application are critical attack surfaces. Weak or misconfigured authentication can lead to unauthorized access.
- Hardware Attack Surface:
- Physical Interfaces: Hardware devices, such as routers, switches, and IoT devices, have physical interfaces that can be targeted by physical attackers or exploited remotely if not properly secured.
- Firmware and Embedded Systems: Devices with firmware or embedded software can be attacked if vulnerabilities are discovered, potentially allowing an attacker to compromise the device’s functionality or data.
- People Attack Surface:
- Social Engineering: Humans are often the weakest link in security. Social engineering attacks, such as phishing, rely on manipulating people into revealing sensitive information or taking specific actions.
- Insider Threats: Malicious or negligent actions by employees or other authorized personnel can pose a significant threat to an organization’s security.
- Cloud and Virtualization Attack Surface:
- Virtual Machines and Containers: Misconfigured virtualization environments, cloud instances, or container orchestrators can expose vulnerabilities.
- Cloud Services: Third-party cloud services, such as storage, databases, and serverless functions, can become attack surfaces if not configured securely.
- Supply Chain Attack Surface:
- Software Dependencies: Software relies on various libraries and dependencies. Vulnerabilities in these dependencies can be exploited, leading to supply chain attacks.
- Third-Party Vendors: Organizations often integrate third-party software or components, and vulnerabilities in these components can affect the overall security.
- Physical Attack Surface:
- Physical Access Points: Physical premises, such as data centers and office buildings, have entry points that can be targeted by physical attackers.
- Hardware Devices: Physical devices, such as keycard readers or biometric scanners, can be exploited if vulnerabilities exist.
- Data Attack Surface:
- Databases: Databases that store sensitive information are a valuable target. Database misconfigurations or vulnerabilities can expose data.
- Data in Transit: Data transferred between systems, especially over unencrypted or insecure channels, can be intercepted and manipulated.
Risk mitigation steps
To effectively manage the attack surface, organizations should adopt a comprehensive strategy that includes the following key steps:
- Identify and Inventory Assets: Begin by identifying and creating an inventory of all assets, including hardware, software, applications, databases, and network components. This step helps you understand the scope of your attack surface.
- Asset Classification: Categorize assets based on their importance and sensitivity to the organization. Not all assets have the same value or require the same level of protection.
- Vulnerability Assessment: Conduct regular vulnerability assessments and penetration testing to identify weaknesses in your systems and applications. This helps you understand where potential threats could exploit the attack surface.
- Reduce and Harden: Implement security best practices and apply necessary patches and updates to reduce vulnerabilities. Harden systems and applications by disabling unnecessary services, using strong authentication, and employing security configurations.
- Access Control: Implement strong access controls and authentication mechanisms to ensure that only authorized personnel and systems can interact with critical assets.
- Monitor and Detect: Continuously monitor the attack surface for unusual activities and potential threats. Security information and event management (SIEM) systems can help with real-time monitoring and threat detection.
- Incident Response: Develop an incident response plan that outlines procedures for handling security incidents. A well-prepared incident response can help mitigate the impact of successful attacks.
- Security Awareness: Educate employees and stakeholders about security best practices and the role they play in reducing the attack surface. Address social engineering and human-related threats through training and awareness programs.
- Third-Party Risk Management: Assess and manage the security of third-party vendors and partners whose products or services interact with your systems. Their vulnerabilities can become part of your attack surface.
- Regular Auditing and Review: Conduct regular security audits and reviews to ensure that security controls are effective and up to date. Adapt your security strategy as threats and technologies evolve.
- Backup and Recovery: Implement robust data backup and recovery strategies to ensure business continuity in case of a security incident.
- Documentation: Maintain documentation of security policies, procedures, and configurations to facilitate ongoing management and auditing.
Managing the attack surface is an ongoing process that requires vigilance and adaptability. As technology evolves and new threats emerge, organizations must continually assess and adjust their security measures to protect against evolving attack vectors.
Collection of Thoughts on Cyber Security

- Biggest AI trends in Cyber -Summary of an interesting article which appeared in CNET reviewing the impact of AI in Cyber security https://www.linkedin.com/feed/update/urn:li:activity:7116886138706878464
NIST Framework
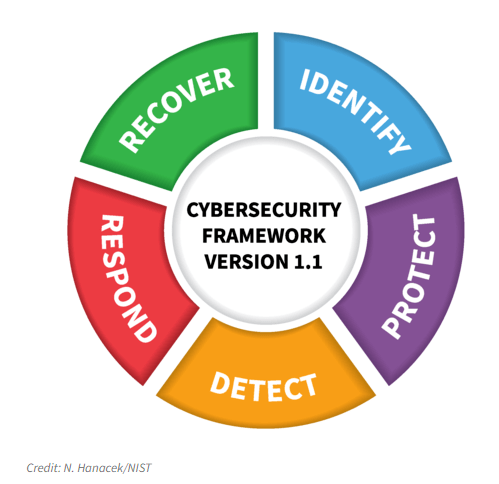
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a comprehensive set of guidelines, best practices, and standards designed to help organizations manage and improve their cybersecurity posture. NIST, part of the U.S. Department of Commerce, developed this framework to provide a structured approach to cybersecurity risk management. Here’s a detailed overview of the NIST Cybersecurity Framework:
1. Framework Core:
The NIST Cybersecurity Framework consists of three key components, with the “Framework Core” at its center. The Framework Core includes functions, categories, and subcategories that serve as the foundation for building and customizing an organization’s cybersecurity program:
- Functions: There are five core functions, each representing a high-level cybersecurity activity. These functions are Identify, Protect, Detect, Respond, and Recover. They form the backbone of the framework and provide a structured way to think about cybersecurity activities.
- Categories: Categories further break down the functions into more specific areas of focus. For example, within the “Protect” function, there are categories such as Access Control, Data Protection, and Awareness and Training.
- Subcategories: Subcategories provide granular guidance on specific actions and controls that organizations can implement to address cybersecurity risks. For instance, a subcategory might specify the use of multi-factor authentication for access control.
2. Framework Implementation Tiers:
The NIST framework defines four implementation tiers that reflect an organization’s cybersecurity risk management practices:
- Tier 1 – Partial: Organizations at this level have an ad-hoc approach to cybersecurity risk management, with limited awareness and minimal formal processes in place.
- Tier 2 – Risk Informed: Organizations at this level have a basic understanding of their cybersecurity risks and have started to develop more formalized processes and policies.
- Tier 3 – Repeatable: Organizations have a well-defined and repeatable approach to managing cybersecurity risks. They have policies and procedures in place, and they regularly review and update their cybersecurity practices.
- Tier 4 – Adaptive: Organizations at this level have a dynamic and adaptive approach to cybersecurity risk management. They continuously monitor and adjust their practices based on changes in the threat landscape and their specific needs.
3. Framework Profiles:
A Framework Profile is a representation of an organization’s current and desired cybersecurity posture. It involves selecting and customizing the framework’s functions, categories, and subcategories to align with the organization’s specific goals, risk tolerance, and resource constraints. Organizations can create different profiles to address different aspects of their cybersecurity program.
4. Framework Implementation:
Implementing the NIST Cybersecurity Framework involves the following steps:
- Prioritize and Scope: Identify critical assets, systems, and data that need protection and determine the scope of your cybersecurity program.
- Create a Current Profile: Assess your current cybersecurity practices and create a profile that reflects your existing posture.
- Set Target Profile(s): Define the desired cybersecurity posture(s) you want to achieve. These should align with your organization’s goals and risk tolerance.
- Identify and Implement Improvements: Identify gaps between the current and target profiles and develop plans to address them. Implement security controls and best practices accordingly.
- Monitor and Adjust: Continuously monitor your cybersecurity program, assess its effectiveness, and make adjustments as necessary to adapt to changing threats and vulnerabilities.
5. Framework Use Cases:
The NIST Cybersecurity Framework can be used in various ways, including:
- Risk Management: It helps organizations identify, assess, and manage cybersecurity risks effectively.
- Communication: It provides a common language for discussing cybersecurity practices and risks within an organization and with external stakeholders.
- Compliance: It assists organizations in aligning with industry regulations and standards, such as HIPAA, GDPR, and others.
- Continuous Improvement: It supports ongoing assessment and improvement of an organization’s cybersecurity posture.
The NIST Cybersecurity Framework is widely recognized and adopted by organizations around the world as a valuable tool for enhancing cybersecurity resilience and managing risks effectively. It provides a flexible and adaptable approach to cybersecurity, making it suitable for organizations of all sizes and industries.
OWASP Top 10

The OWASP Top Ten is a regularly updated list of the ten most critical web application security risks. It’s created and maintained by the Open Web Application Security Project (OWASP), a nonprofit organization focused on improving the security of software. The OWASP Top Ten serves as a valuable resource for developers, security professionals, and organizations to understand and mitigate common web application vulnerabilities.
The latest list of OWASP top 10 is available at the following link https://owasp.org/Top10/
The OWASP (Open Web Application Security Project) Top Ten is highly important in the field of web application security for several reasons:
- Risk Prioritization: The OWASP Top Ten provides a concise list of the most critical web application security risks. This prioritization helps organizations focus their resources on addressing the most significant threats, reducing the chances of a successful attack.
- Awareness: It raises awareness about common web application vulnerabilities and attack vectors among developers, security professionals, and decision-makers. This awareness is essential for proactive risk mitigation.
- Educational Resource: The OWASP Top Ten serves as an educational resource. It offers detailed information about each security risk, including examples and recommended countermeasures. Developers and security practitioners can use it as a reference guide to understand and mitigate vulnerabilities.
- Baseline for Security Testing: Organizations often use the OWASP Top Ten as a baseline for security testing. It helps assess the security posture of web applications and identify vulnerabilities that need immediate attention.
- Compliance and Regulations: Many industry regulations and standards reference the OWASP Top Ten as a benchmark for web application security. Complying with these regulations often requires addressing the vulnerabilities listed in the OWASP Top Ten.
- Risk Mitigation: By addressing the vulnerabilities listed in the OWASP Top Ten, organizations can significantly reduce the risk of data breaches, financial losses, and reputational damage resulting from web application attacks.
- Continuous Improvement: The list is updated periodically to reflect emerging threats and changes in technology. This encourages organizations to stay current with evolving security challenges and continuously improve their security measures.
- Open Source and Community-Driven: OWASP is an open-source community-driven initiative. This means that the knowledge and resources provided by the OWASP Top Ten are freely accessible and constantly evolving with input from the global security community.
- Cross-Platform Applicability: The OWASP Top Ten is technology-agnostic and applicable to various web application development platforms and programming languages. It provides guidance that can be adapted to a wide range of web applications.
- Reduced Development Costs: By addressing security risks early in the development process, organizations can avoid costly security fixes and emergency responses after an application is in production. This leads to cost savings in the long run.
In summary, the OWASP Top Ten is a foundational resource for web application security. It helps organizations identify, prioritize, and mitigate the most critical security risks, ultimately enhancing the security posture of web applications and reducing the likelihood of successful cyberattacks.
Information Security – Frameworks

Numerous cybersecurity frameworks and standards exist to help organizations establish, manage, and improve their cybersecurity programs. These frameworks provide guidelines, best practices, and structured approaches to addressing cybersecurity risks. Here are some of the most widely recognized and used cybersecurity frameworks:
- NIST Cybersecurity Framework (NIST CSF): Developed by the U.S. National Institute of Standards and Technology (NIST), this framework provides a comprehensive approach to managing cybersecurity risk. It consists of five core functions: Identify, Protect, Detect, Respond, and Recover. The NIST CSF is widely adopted and adaptable to various sectors.
- ISO/IEC 27001 and 27002: The ISO/IEC 27000 series provides a globally recognized framework for information security management systems (ISMS). ISO/IEC 27001 specifies the requirements for establishing, implementing, maintaining, and continually improving an ISMS, while ISO/IEC 27002 offers guidelines for implementing security controls.
- Center for Internet Security (CIS) Controls: Formerly known as the SANS Critical Security Controls, the CIS Controls are a set of prioritized, actionable best practices for securing an organization’s information systems. They focus on foundational security measures.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards designed to ensure the secure handling of credit card information. It applies to organizations that process payment card transactions.
- Cloud Security Alliance (CSA) Cloud Controls Matrix: This framework provides a set of security principles and best practices for securing cloud computing environments. It helps organizations evaluate and mitigate risks associated with cloud adoption.
- CIS Top 20 Critical Security Controls (CIS CSC): This is a prioritized list of security actions that organizations can take to improve their cybersecurity posture. It focuses on reducing the attack surface and increasing resilience against cyber threats.
- NIST Risk Management Framework (NIST RMF): Designed for federal agencies and contractors, NIST RMF provides a structured process for managing cybersecurity risk. It aligns with NIST’s broader cybersecurity framework.
- ITIL (Information Technology Infrastructure Library): ITIL is a set of practices for IT service management. While not specific to cybersecurity, it includes guidance on managing IT services securely and ensuring business continuity.
- FAIR (Factor Analysis of Information Risk): FAIR is a framework for understanding, analyzing, and quantifying information risk in financial terms. It helps organizations make informed decisions about risk management.
- Cobit (Control Objectives for Information and Related Technologies): Developed by ISACA, Cobit provides a framework for governing and managing enterprise IT processes. It includes security and risk management components.
- CERT Resilience Management Model (CERT-RMM): Created by Carnegie Mellon University’s Software Engineering Institute, CERT-RMM focuses on building organizational resilience by managing security and operational risks.
- ISA/IEC 62443: This series of standards provides cybersecurity guidelines for industrial automation and control systems (IACS) and is widely used in sectors like manufacturing and critical infrastructure.
These frameworks serve various purposes, from general cybersecurity risk management to industry-specific guidance. Organizations often select and adapt one or more of these frameworks based on their unique needs, compliance requirements, and the nature of their operations. Implementing a cybersecurity framework helps organizations identify and address vulnerabilities, establish best practices, and continuously improve their cybersecurity posture.
Cyber Kill Chain
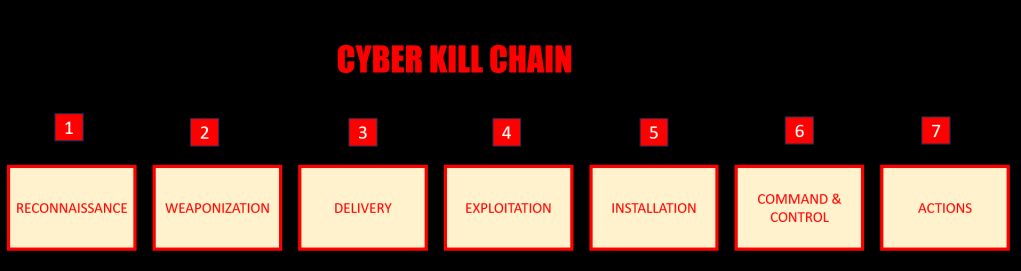
The Cyber Kill Chain is a concept in cybersecurity that describes the stages of a cyberattack, from the initial reconnaissance phase to the final objective, which is often data theft, system compromise, or other malicious actions. Developed by Lockheed Martin, the Cyber Kill Chain framework helps organizations understand and visualize the typical steps attackers take to achieve their goals. By analyzing and disrupting these stages, organizations can enhance their cybersecurity defenses. The Cyber Kill Chain typically consists of seven stages:
1. Reconnaissance:
In this initial stage, attackers gather information about their target. This might involve passive activities like searching the internet, scanning public websites, and social engineering to gather information about the target’s employees, systems, and vulnerabilities.
2. Weaponization:
After gathering information, attackers move to weaponization. They create or acquire malicious tools or payloads, such as malware, viruses, or exploit kits, designed to exploit specific vulnerabilities in the target’s systems.
3. Delivery:
In this stage, attackers deliver the weaponized payload to the target. Common delivery methods include phishing emails, malicious attachments, infected websites, or other means to get the malware onto the target’s network or system.
4. Exploitation:
Once the malicious payload is delivered and executed on the target’s system, the attacker exploits vulnerabilities to establish a foothold within the network. This stage often involves the exploitation of known software vulnerabilities or the use of zero-day exploits.
5. Installation:
After successful exploitation, the attacker installs backdoors, rootkits, or other malicious software on the compromised system. This allows them to maintain access and control over the victim’s network.
6. Command and Control (C2):
Attackers establish communication channels with the compromised systems to control and manage their malicious activities. They use these channels to send commands, exfiltrate data, and maintain persistence.
7. Actions on Objectives:
Finally, in the last stage, attackers carry out their primary objectives, which could include data theft, data manipulation, system disruption, or any other malicious actions they intended to achieve.
The Value of the Cyber Kill Chain:
Understanding the Cyber Kill Chain is valuable for several reasons:
- Threat Detection: By recognizing the stages of an attack, organizations can detect and respond to threats at various points in the chain, rather than waiting for an attack to reach its final stages.
- Risk Assessment: Analyzing the Kill Chain can help organizations identify vulnerabilities and weaknesses in their security posture, allowing for proactive risk mitigation.
- Incident Response: Understanding an attacker’s progression through the Kill Chain can inform incident response efforts, enabling organizations to disrupt attacks before they cause significant harm.
- Security Planning: The Kill Chain concept can guide the development of cybersecurity strategies and the selection of security technologies and practices to thwart potential threats.
It’s important to note that while the Cyber Kill Chain provides a valuable framework, not all attacks follow this linear path, and sophisticated adversaries may employ tactics to bypass or disrupt traditional defence mechanisms. Consequently, organizations often supplement the Kill Chain with additional cybersecurity models and strategies to create a comprehensive defence posture.
Cyber Security CIA Triad

The CIA Triad, in the context of cybersecurity, is a fundamental framework that defines the core principles of information security. It stands for Confidentiality, Integrity, and Availability. These three principles form the cornerstone of any effective cybersecurity strategy and guide the implementation of security measures to protect digital assets, systems, and data.
1. Confidentiality:
Confidentiality focuses on ensuring that sensitive information remains private and accessible only to authorized individuals, systems, or processes. This principle aims to prevent unauthorized access, disclosure, or leakage of sensitive data. Key aspects of confidentiality include:
- Data Encryption: Encrypting data ensures that even if unauthorized parties gain access to it, they cannot understand or use the information without the decryption key.
- Access Control: Implementing access controls, such as user authentication and authorization mechanisms, restricts access to data and systems based on user roles and permissions.
- Data Classification: Classifying data based on its sensitivity allows organizations to prioritize protection efforts and apply appropriate security controls to different types of data.
- Secure Communication: Protecting the confidentiality of data during transmission through secure communication protocols like HTTPS or VPNs.
2. Integrity:
Integrity ensures the accuracy, consistency, and reliability of data and systems. It ensures that data is not altered, tampered with, or corrupted, whether intentionally or accidentally. Key aspects of integrity include:
- Data Validation: Implementing data validation checks to ensure that data is accurate and consistent, preventing input errors and tampering.
- Digital Signatures: Using digital signatures to verify the authenticity and integrity of messages or files. Digital signatures provide a way to detect unauthorized changes to data.
- Change Management: Managing changes to systems and data through controlled processes and version control to prevent unintended modifications.
- Data Backups: Regularly backing up data to protect against data loss or corruption and ensuring that backup copies maintain data integrity.
3. Availability:
Availability focuses on ensuring that systems, data, and resources are available and accessible when needed by authorized users. This principle addresses the prevention of disruptions, downtime, or denial of service attacks. Key aspects of availability include:
- Redundancy: Employing redundancy in systems and networks to maintain operations even in the face of hardware failures or other disruptions.
- Load Balancing: Distributing network traffic across multiple servers to prevent overload and maintain service availability.
- Disaster Recovery: Developing and testing disaster recovery plans to recover systems and data in the event of natural disasters, cyberattacks, or other disruptions.
- Distributed Denial of Service (DDoS) Mitigation: Implementing measures to detect and mitigate DDoS attacks that can overwhelm and disrupt online services.
- Monitoring and Alerting: Continuously monitoring systems for signs of potential issues and setting up alerting mechanisms to respond promptly to anomalies or incidents.
The CIA Triad provides a structured approach to cybersecurity by emphasizing the importance of maintaining a balance between these three principles. It helps organizations identify security risks and select appropriate security controls to protect their digital assets effectively. While the CIA Triad serves as a foundational framework, additional principles and frameworks, such as non-repudiation and the Zero Trust model, can complement and enhance an organization’s overall cybersecurity strategy.
